Imagine yourself working on an important document, suddenly your screen goes all black and a message pops up “Oops, your files have been encrypted!” You restart your computer, but no luck. One by one, the same happens with all the computers in your organization. Distressful, isn’t it?
In May 2017, something similar happened when 300,000 computers running on Microsoft Windows operating system were cyber attacked by a ransomware. This malicious software encrypted data of users across the world, which can only be released in exchange of a ransom payment.
According to a research by Identity Theft Resource Centre (ITRC) and CyberScout, the number of data breaches in the US hit an all-time record high of 1093 in 2016, 40% up from the previous year.
As technology is increasing at a rapid pace, internet has become the primary space for storing global information. Since then tackling with security breaches has become the top most priority for business and government across the globe.
Ethical hacking has emerged as a proactive solution for this worldwide issue:
From the above discussion, it is clear that pretty much every organization is vulnerable to cyber-attacks. Time, resources and expert opinion are some of the few reasons why organizations are shifting to researchers (aka ethical hackers) to test their internal coding.
These ethical hackers test and discover flaws in your software/website, which were either overlooked by developers or missed by the organization’s security team. An ethical hacker privately reports the vulnerability to the organization and allows them a reasonable time to fix the issue.
To connect organizations with ethical hackers and provide them a seamless & reliable communication channel, today, there are several bug bounty and vulnerability disclosure websites. And given the frequency of cyber-attacks happening these days, there’s also a huge need of such platforms.
So, for entrepreneurs eyeing to launch such an online startup, here is detailed analysis of its business model, revenue model & critical website features.
Business Model Overview
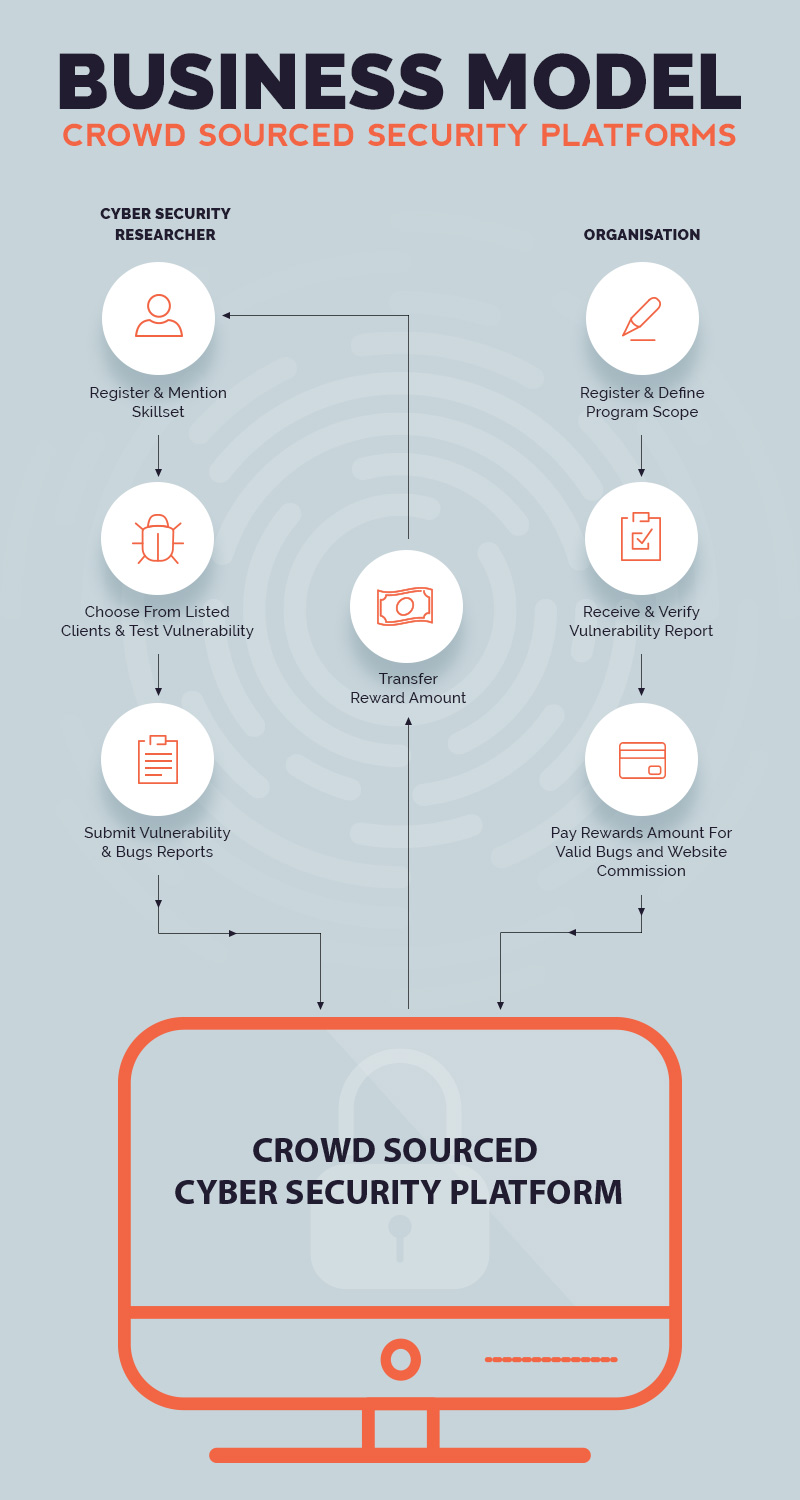
As discussed above, these crowd-sourced security websites have become the need of the hour. There might be some companies who have a security team in place but they do not want to risk the chances of any security breach. The main motive of crowd-sourced security websites is to connect companies with ethical hackers. The website acts as a middleman for communication between the two entities.
Below we have mentioned step wise functioning of these sites for both researchers and companies:
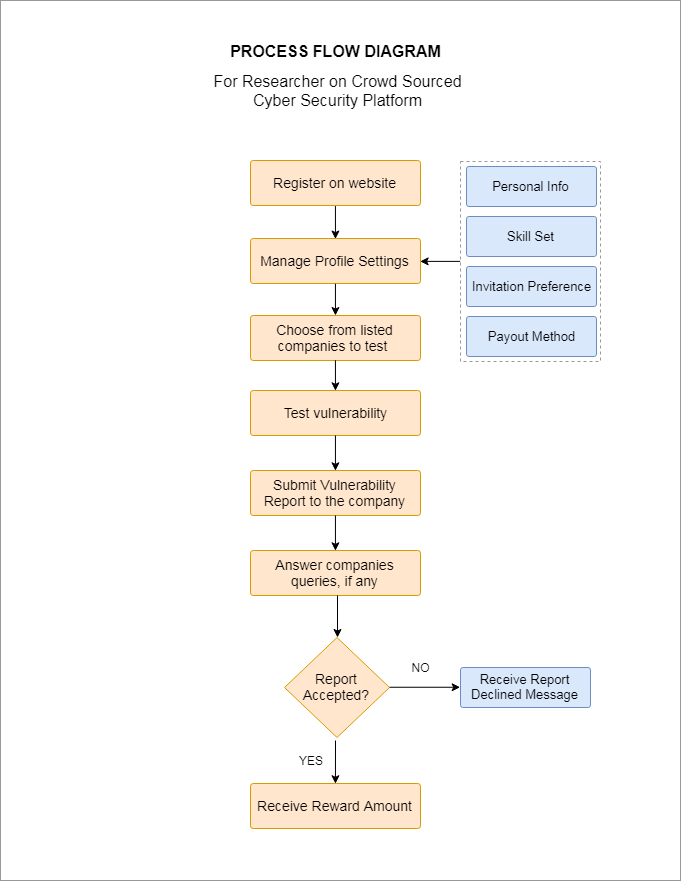
How it works for researchers:
- Step 1: – Register with the website
- Step 2: – Browse through the clients listed on the website
- Step 3: – Choose which company you are going to test and find vulnerability
- Step 4: – Once you find the vulnerability, make a submission
- Step 4: – Once the report is submitted you can communicate directly with the company
- Step 5: – As soon as the company accepts your report, you will receive the payment
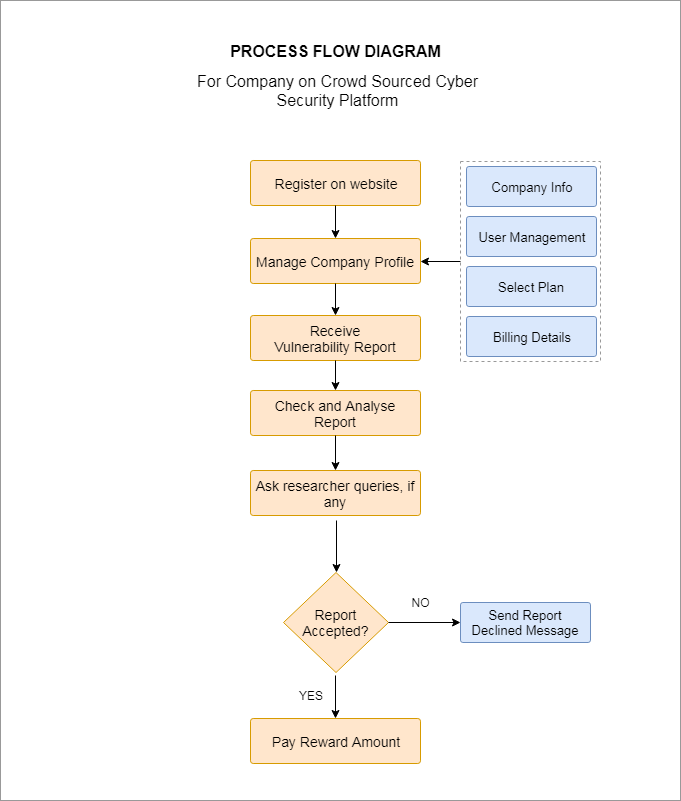
How it works for companies:
- Step 1: – Register with the website
- Step 2: – Select the type of project
- Step 3: – Select the scope of the project
- Step 4: – Mention the reward amount
- Step 5: – All incoming reports are first checked by the website for relevance and scope
- Step 6: – Check the report sent by the ethical hacker
- Step 7: – Verify the report and vulnerability and pay the already mentioned reward
Major market players:
- Hackerone
- Intigriti
- Crowd Shield
- Tarlogic
- Synack
Revenue Model
Primary Revenue Model
Commission
Since the website acts as the middleman that connects the ethical hackers with companies, the primary source of revenue is commission. When the company pays the bounty or reward to the researchers a certain percentage is cut by the website owner.
Secondary revenue channels
Advertisement
The traffic on crowd sourced security platforms is usually high. People not only visit crowd sourced security websites to approach a researcher, but also to gather knowledge (about the common bugs & security issues). For this reason, advertising can be huge source of income.
Membership
Website can allow extra benefits and services to users who have paid extra to be a member of the website.
Also read: Make your website 2017 ready with latest design and technology trends
Critical Website Features
Hacker Leaderboard
A hacker leaderboard is an essential feature where the basic information of all the ethical hackers who have registered on the website is present. To check whether the website has good ethical hackers, companies can refer to the hacker leaderboard and check the top 10 ethical hackers. The leaderboard can also inspire competition between the ethical hackers, motivating them to find & fix more vulnerability.
Hacker Challenges
Many companies after releasing software or software update challenge ethical hackers to find vulnerabilities in the system. Companies can run short-term challenges to identify more unique, severe vulnerability than traditional offerings like pen-test.
Bug Bounty Program
Companies run a bug bounty program, which rewards individuals for discovering and reporting software bugs. Whenever a researcher finds a bug/vulnerability which has potential to be exploited, it is reported to the company and after thorough analysis from the company, a bounty/cash reward is paid to the researcher. Payment amount is decided according to the size of the organization, the difficulty in hacking the system and the impact on users.
Response to Third-party Penetration
There are cases when non-ethical hackers get to know a vulnerability of certain company. Before the company security is breached by the hacker, the company can contact ethical hackers from the website to receive, respond and resolve those security vulnerabilities. This ensures that third-party reports are reached to the right person in the organization and also makes sure company’s internal security team is aware of software vulnerability that the world has discovered.
Suggested Read: Best Security Tips from Pro Developers to Protect Website from Hackers
Case Study/Guides
Case studies and guides on crowd sourced security websites depict that the website also possesses knowledge resources of how to avoid a security breach. Common bugs and vulnerability can be listed and discussed about to make new comers aware on how to stay secure from hackers. Trends, facts, tips, reports, success stories can be helpful for building a trust factor with the companies and also to impart knowledge.
Trust factors
Crowd sourced security websites have to build trust with companies and ethical hackers. To ensure the company that they will get optimal service and to ensure the researchers that they will be paid for the hard work they have put in, crowd sourced security website should add trust inducing features. Listing the companies who have partnered, showcasing their testimonials, number of bugs fixed, amount of bounty paid, and reviews will help in building the trust.
FAQs
The uniqueness of the business model can make it difficult to understand for the company and researchers. To address their concerns, you can prepare a comprehensive Q/A section that will cover the challenges faced by companies and researches related to using your website. Also provide a section where they can ask their specific queries.
Recommended Reading: Security Measures Online Businesses Should Take to Keep User Data Safe
Conclusion
The ubiquity of cyber-attacks and impossible attempts of organizations to prevent them is persuading big organization to turn towards crowd sourced security websites for a solution. Though the demand for ethical hackers is huge, the bug bounty industry is still in its nascent stage. The above-mentioned features will help you launch a perfect platform according to the needs of the clients and the researchers.
How much launching a crowd-sourced security website will cost?




